

Attacks on wireless networks are increasing daily with the increasing use of wireless networks. The encryption of information before it is transmitted on a wireless network is the most popular method of protecting wireless networks against attackers.
There are several types of wireless encryption algorithms that can secure a wireless network. Each wireless encryption algorithm has advantages and disadvantages.
802.11i: It is an IEEE amendment that specifies security mechanisms for 802.11 wireless networks.
WEP: WEP is an encryption algorithm for IEEE 802.11 wireless networks. It is an old wireless security standard and can be cracked easily.
EAP: The Extensible Authentication Protocol (EAP) supports multiple authentication methods, such as token cards, Kerberos, and certificates.
LEAP: Lightweight EAP (LEAP) is a proprietary version of EAP developed by Cisco.
WPA: It is an advanced wireless encryption protocol using TKIP and Message Integrity Check (MIC) to provide strong encryption and authentication. It uses a 48-bit initialization vector (IV), 32-bit cyclic redundancy check (CRC), and TKIP encryption for wireless security.
TKIP: It is a security protocol used in WPA as a replacement for WEP.
WPA2: It is an upgrade to WPA using AES and the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) for wireless data encryption.
AES: It is a symmetric-key encryption used in WPA2 as a replacement for TKIP.
CCMP: It is an encryption protocol used in WPA2 for strong encryption and authentication.
WPA2 Enterprise: It integrates EAP standards with WPA2 encryption.
RADIUS: It is a centralized authentication and authorization management system.
PEAP: It is a protocol that encapsulates the EAP within an encrypted and authenticated Transport Layer Security (TLS) tunnel.
WPA3: It is a third-generation Wi-Fi security protocol that provides new features for personal and enterprise usage. It uses Galois/Counter Mode-256 (GCMP-256) for encryption and the 384-bit hash message authentication code with the Secure Hash Algorithm (HMAC-SHA-384) for authentication.

WEP was an early attempt to protect wireless networks from security breaches, but as technology improved, it became evident that information encrypted with WEP is vulnerable to attack. We discuss WEP in detail here.
What is WEP Encryption?
WEP is a component of the IEEE 802.11 WLAN standards. Its primary purpose is to ensure data confidentiality
on wireless networks at a level equivalent to that of wired LANs, which
can use physical security to stop unauthorized access to a network.
In a WLAN, a user or an attacker can access the network without physically connecting to the LAN. Therefore, WEP utilizes an encryption mechanism at the data link layer for minimizing unauthorized access to the WLAN. This is accomplished by encrypting data with the symmetric Rivest Cipher 4 (RC4) encryption algorithm, which is a cryptographic mechanism used to defend against threats.
Role of WEP in Wireless Communication
WEP protects against eavesdropping on wireless communications.
It attempts to prevent unauthorized access to a wireless network.
It depends on a secret key shared by a mobile station and an AP. This key encrypts packets before transmission. Performing an integrity check ensures that packets are not altered during transmission. 802.11 WEP encrypts only the data between network clients.
Main Advantages of WEP
Confidentiality: It prevents link-layer eavesdropping.
Access Control: It determines who may access data.
Data Integrity: It protects the change of data by a third party.
Efficiency
Key Points
WEP
was developed without any academic or public review. In particular, it
was not reviewed by cryptologists during development. Therefore, it has significant vulnerabilities and design flaws.
WEP is a stream cipher that uses RC4 to produce a stream of bytes that are XORed with plaintext. The length of the WEP and secret key are as follows:
64-bit WEP uses a 40-bit key
128-bit WEP uses a 104-bit key
256-bit WEP uses 232-bit key
Flaws of WEP
The following basic flaws undermine WEP’s ability to protect against a serious attack.
No defined method for encryption key distribution:
- Pre-shared keys (PSKs) are set once at installation and are rarely (if ever) changed.
- It is easy to recover the number of plaintext messages encrypted with the same key.
RC4 was designed to be used in a more randomized environment than that utilized by WEP:
- As the PSK is rarely changed, the same key is used repeatedly.
- An attacker monitors the traffic and finds different ways to work with the plaintext message.
- With knowledge of the ciphertext and plaintext, an attacker can compute the key.
Attackers analyze the traffic from passive data captures and crack WEP keys with the help of tools such as AirSnort and WEPCrack.
Key scheduling algorithms are also vulnerable to attack.
How WEP Works
CRC-32 checksum is used to calculate a 32-bit integrity check value (ICV) for the data, which, in turn, is added to the data frame.
A 24-bit arbitrary number known as the initialization vector (IV) is added to the WEP key; the WEP key and IV are together called the WEP seed.
The WEP seed is used as the input to the RC4 algorithm to generate a keystream, which is bit-wise XORed with a combination of the data and ICV to produce the encrypted data.
The IV field (IV + PAD + KID) is added to the ciphertext to generate a MAC frame.

Figure 8.5: Operational flow of WEP
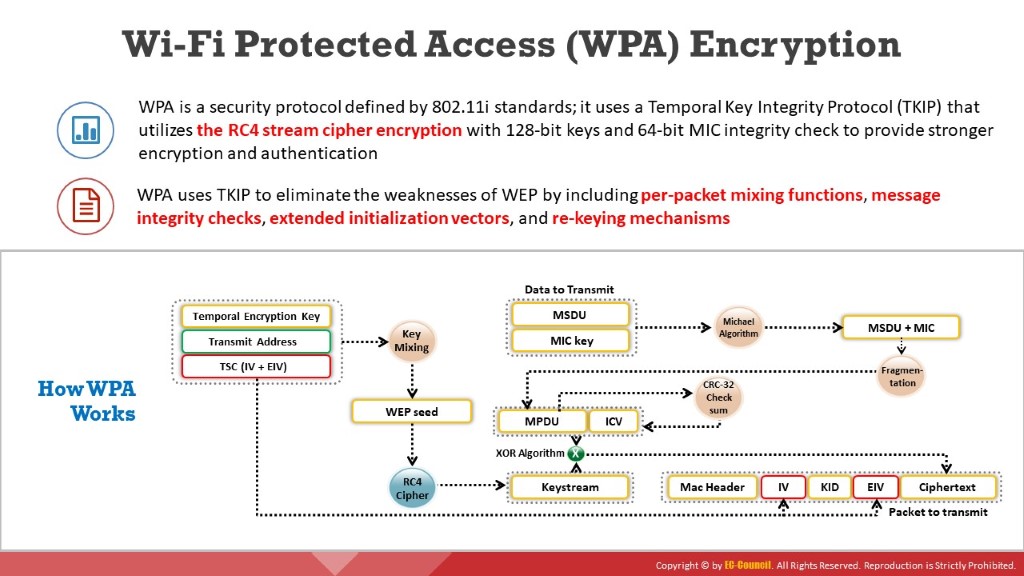
Wi-Fi Protected Access (WPA) is a security protocol defined by the 802.11i standard. In the past, the primary security mechanism used between wireless APs and wireless clients was WEP encryption, which has a major drawback in that it uses a static encryption key. An attacker can exploit this weakness using tools that are freely available on the Internet. IEEE defines WPA as “an expansion to the 802.11 protocols that can allow for increased security.” Nearly every Wi-Fi manufacturer provides WPA.
WPA has better data encryption security than WEP because messages pass through a Message Integrity Check (MIC) using the Temporal Key Integrity Protocol (TKIP), which utilizes the RC4 stream cipher encryption with 128-bit keys and 64-bit MIC to provide strong encryption and authentication. WPA is an example of how 802.11i provides stronger encryption and enables pre-shared key (PSK) or EAP authentication. WPA uses TKIP for data encryption, which eliminates the weaknesses of WEP by including per-packet mixing functions, MICs, extended IVs and re-keying mechanisms.
WEP normally uses a 40-bit or 104-bit encryption key, whereas TKIP uses 128-bit keys for each packet. The MIC for WPA prevents the attacker from changing or resending the packets.
TKIP: It is used in a unicast encryption key that changes for every packet, thereby enhancing security. This change in the key for each packet is automatically coordinated between the wireless client and AP. TKIP uses a Michael Integrity Check algorithm with an MIC key to generate the MIC value. It utilizes the RC4 stream cipher encryption with 128-bit keys and a 64-bit MIC integrity check. It mitigates vulnerability by increasing the size of the IV and using mixing functions. Under TKIP, the client starts with a 128-bit temporal key (TK) that is then combined with the client's MAC address and with an IV to create a keystream that is used to encrypt data via RC4. It implements a sequence counter to protect against replay attacks. TKIP enhances WEP by adding a rekeying mechanism to provide fresh encryption and integrity keys. TKs are changed every 10,000 packets, which makes TKIP-protected networks more resistant to cryptanalytic attacks involving key reuse.
TKs: All newly deployed Wi-Fi equipment uses either TKIP (for WPA) or AES (for WPA2) encryption to ensure WLAN security. In the WEP encryption mechanism, the protocol derives encryption keys (TKs) from the pairwise master key (PMK), which is created during the EAP authentication session, whereas in the WPA and WPA2 encryption mechanisms, the protocol obtains the encryption keys during a four-way handshake. In the EAP success message, the PMK is sent to the AP but is not directed to the Wi-Fi client because it has derived its own copy of the PMK.
The below figure shows the installation procedure for TKs.

Figure 8.6: Operational flow of temporal keys
- AP sends an ANonce to the client, which uses it to construct the pairwise transient key (PTK).
- The client responds with its own Nonce value (SNonce) to the AP, together with an MIC.
- The AP sends the group temporal key (GTK) and a sequence number, together with another MIC, which is used in the next broadcast frames.
- The client confirms that the temporal keys are installed.
How WPA Works
A TK, transmit address, and TKIP sequence counter (TSC) are used as input to the RC4 algorithm to generate a keystream.
- The IV or TK sequence, transmit address or MAC destination address, and TK are combined with a hash function or mixing function to generate a 128-bit and 104-bit key.
- This key is then combined with RC4 to produce the keystream, which should be of the same length as the original message.
The MAC service data unit (MSDU) and message integrity check (MIC) are combined using the Michael algorithm.
The combination of MSDU and MIC is fragmented to generate the MAC protocol data unit (MPDU).
A 32-bit ICV is calculated for the MPDU.
The combination of MPDU and ICV is bitwise XORed with the keystream to produce the encrypted data.
The IV is added to the encrypted data to generate the MAC frame.
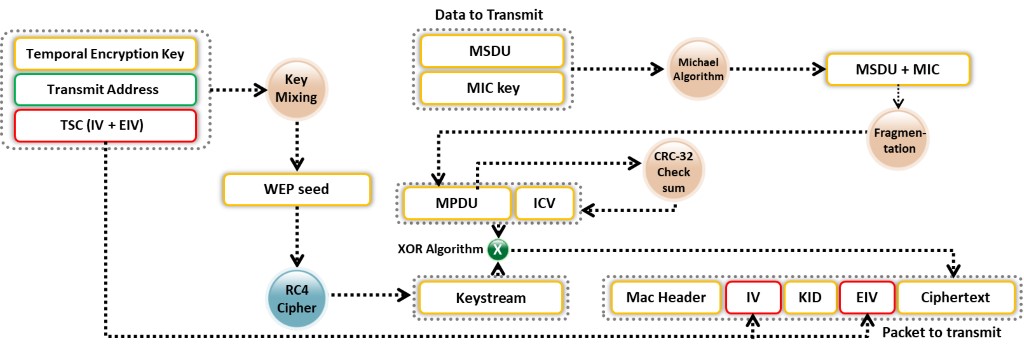
Figure 8.7: Operational flow of WPA

Wi-Fi Protected Access 2 (WPA2) is a security protocol used to safeguard wireless networks. WPA2 replaced WPA in 2006. It is compatible with the 802.11i standard and supports many security features that WPA does not. WPA2 introduces the use of the National Institute of Standards and Technology (NIST) FIPS 140-2-compliant AES encryption algorithm, which is a strong wireless encryption algorithm, and the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP). It provides stronger data protection and network access control than WPA. Furthermore, it gives a high level of security to Wi-Fi connections so that only authorized users can access the network.
Modes of Operation
WPA2 offers two modes of operation:
WPA2-Personal: WPA2-Personal uses a password set in advance, called the pre-shared key (PSK), to protect unauthorized network access. Each wireless device uses the same 256-bit key generated from a password to authenticate with the AP. In the PSK mode, each wireless network device encrypts the network traffic using a 128-bit key derived from a passphrase of 8–63 ASCII characters. The router uses the combination of a passphrase, network SSID, and TKIP to generate a unique encryption key for each wireless client. These encryption keys change continually.
WPA2-Enterprise: WPA2-Enterprise uses EAP or RADIUS for centralized client authentication using multiple authentication methods, such as token cards, Kerberos, and certificates. WPA-Enterprise assigns a unique ciphered key to every system and hides it from the user in order to provide additional security and to prevent the sharing of keys. Users are allocated login credentials by a centralized server, which they must present when connecting to the network.
How WPA2 Works
During
CCMP implementation, additional authentication data (AAD) are generated
using a MAC header and included in the encryption process that uses
both AES and CCMP encryptions. Consequently, the non-encrypted portion
of the frame is protected from any alteration or distortion. The
protocol uses a sequenced packet number (PN) and a portion of the MAC
header to generate a Nonce that it uses in the encryption process. The
protocol gives plaintext data, and temporal keys, AAD, and Nonce are
used as input for the data encryption process that uses both AES and
CCMP algorithms.
A PN is included in the CCMP header for protection against replay attacks. The resultant data from the AES and CCMP algorithms produce encrypted text and an encrypted MIC value. Finally, the assembled MAC header, CCMP header, encrypted data, and encrypted MIC form the WPA2 MAC frame. The below figure shows the operational flow of WPA2.

Figure 8.8: Operational flow of WPA2
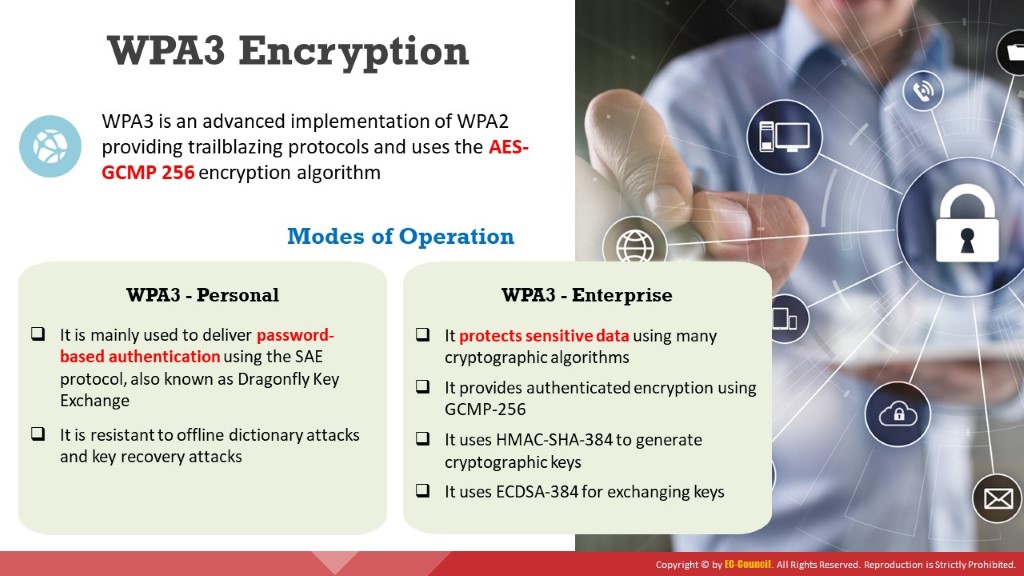
Wi-Fi Protected Access 3 (WPA3) was announced by the Wi-Fi Alliance on January 2018 as an advanced implementation of WPA2 that provides trailblazing protocols. Like WPA2, the WPA3 protocol has two variants: WPA3-Personal and WPA3-Enterprise.
WPA3 provides cutting-edge features to simplify Wi-Fi security and provides the capabilities necessary to support different network deployments ranging from corporate networks to home networks. It also ensures cryptographic consistency using encryption algorithms such as AES and TKIP to defend against network attacks. Furthermore, it provides network resilience through Protected Management Frames (PMF) that deliver a high level of protection against eavesdropping and forging attacks. WPA3 also disallows outdated legacy protocols.
Modes of Operation
WPA3 offers two modes of operation:
WPA3-Personal: This mode is mainly used to deliver password-based authentication. WPA3 is more rigid to attacks than WPA2 because it uses a modern key establishment protocol called the Simultaneous Authentication of Equals (SAE), also known as Dragonfly Key Exchange, which replaces the PSK concept used in WPA2-Personal. Some of the features of WPA3-Personal are described below.
- Resistance to offline dictionary attacks: It prevents passive password attacks such as brute-forcing.
- Resistance to key recovery: Even when a password is determined, it is impossible to capture and determine session keys while maintaining the forward secrecy of network traffic.
- Natural password choice: It allows users to choose weak or popular phrases as passwords, which are easy to remember.
- Easy accessibility: It can provide greater protection than WPA2 without changing the previous methods used by users for connecting to a network.
WPA3-Enterprise: This mode is based on WPA2. It offers better security than WPA2 across the network and protects sensitive data using many cryptographic concepts and tools. Some of the security protocols used by WPA3-Enterprise are described below.
- Authenticated encryption: It helps in maintaining the authenticity and confidentiality of data. For this purpose, WPA3 uses the 256-bit Galois/Counter Mode Protocol (GCMP-256).
- Key derivation and validation: It helps in generating a cryptographic key from a password or master key. It uses the 384-bit hashed message authentication mode (HMAC) with the Secure Hash Algorithm, termed HMAC-SHA-384.
- Key establishment and verification: It helps in exchanging cryptographic keys among two parties. For this purpose, WPA3 uses Elliptic Curve Diffie–Hellman (ECDH) exchange and Elliptic Curve Digital Signature Algorithm (ECDSA) using a 384-bit elliptic curve.
- Frame protection and robust administration: WPA3 uses 256-bit Broadcast/Multicast Integrity Protocol Galois Message Authentication Code (BIP-GMAC-256) for this purpose.
Enhancements in WPA3 with Respect to WPA2
WPA3
can be used to implement a layered security strategy that can protect
all aspects of a Wi-Fi network. WPA3 has a certification program that
specifies the prevailing standards the product must support. The
Dragonfly handshake/SAE protocol is mandatory for WPA3 certification.
The important features of WPA3 are as follows.
Secured handshake: The Simultaneous Authentication of Equals (SAE) protocol, also known as the Dragonfly handshake, can be used to make a password resistant to dictionary and brute-force attacks, preventing the offline decryption of data.
Wi-Fi Easy Connect: This feature simplifies the security configuration process by managing different interface connections in a network with one interface using the Wi-Fi Device Provisioning Protocol (DPP). This can securely allow a plethora of smart devices in a network to connect to one device using a quick response (QR) code or password. It also helps set up a connection between different IoT devices.
Unauthenticated encryption: It uses a new feature called Opportunistic Wireless Encryption (OWE) that replaces the 802.11 “open” authentication by providing better protection when using public hotspots and public networks.
Bigger session keys: The cryptographic security process of WPA3-Enterprise supports key sizes of 192 bits or higher, which are difficult to crack, ensuring rigid protection.
WEP provides data confidentiality on wireless networks, but it is weak and fails to meet any of its security goals. While WPA fixes most of WEP’s problems, WPA2 makes wireless networks almost as secure as wired networks. Because WPA2 supports authentication, only authorized users can access the network. WEP should be replaced with either WPA or WPA2 to secure a Wi-Fi network. Though WPA and WPA2 incorporate protections against forgery and replay attacks, WPA3 can provide a more enhanced password-protection mechanism and secure IoT connections; further, it utilizes stronger encryption techniques. The below table compares WEP, WPA, WPA2, and WPA3 in terms of the encryption algorithm used, the encryption-key size, the initialization vector (IV) it produces, key management, and data integrity.
|
Encryption |
Attributes |
||||
|
Encryption Algorithm |
IV Size |
Encryption Key Length |
Key Management |
Integrity Check Mechanism |
|
|
WEP |
RC4 |
24-bits |
40/104-bits |
None |
CRC-32 |
|
WPA |
RC4, TKIP |
48-bits |
128-bits |
4-way handshake |
Michael algorithm and CRC-32 |
|
WPA2 |
AES-CCMP |
48-bits |
128-bits |
4-way handshake |
CBC-MAC |
|
WPA3 |
AES-GCMP 256 |
Arbitrary length 1 - 264 |
192-bits |
ECDH and ECDSA |
BIP-GMAC-256 |