

An attacker performs vulnerability scanning to identify security loopholes in the target network that they can exploit to launch attacks. Security analysts can use vulnerability assessment tools to identify weaknesses present in the organization’s security posture and remediate the identified vulnerabilities before an attacker exploits them.
Network vulnerability scanners help to analyze and identify vulnerabilities in the target network or network resources by using vulnerability assessment and network auditing. These tools also assist in overcoming weaknesses in the network by suggesting various remediation techniques.
The following are some of the most effective vulnerability assessment tools:
-
-
- Qualys Vulnerability Management
-
Source: https://www.qualys.com
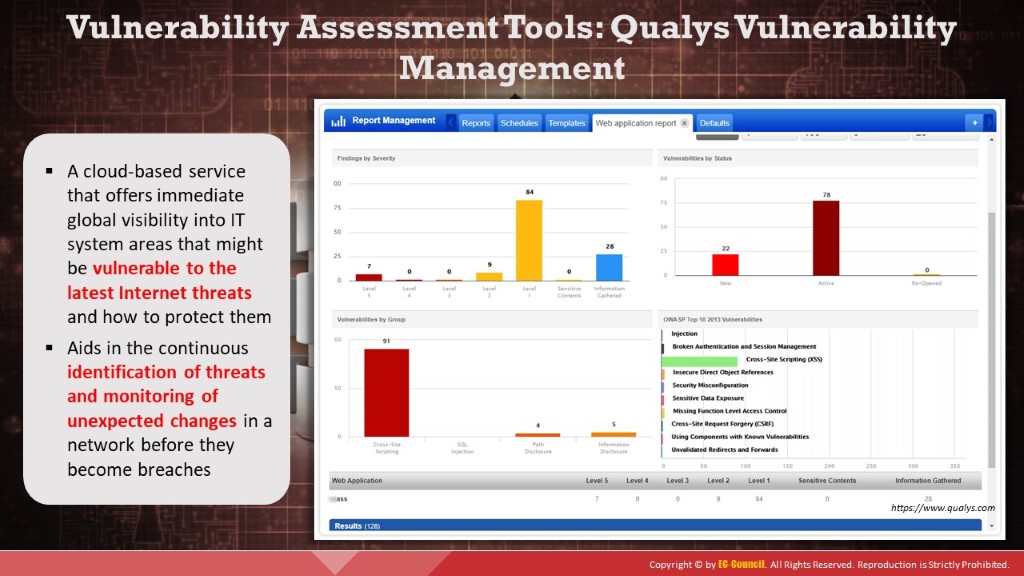
Qualys VM is a cloud-based service that gives immediate, global visibility into where IT systems might be vulnerable to the latest Internet threats and how to protect them. It helps to continuously identify threats and monitor unexpected changes in a network before they turn into breaches.

Figure 3.17: Vulnerability scanning using Qualys Vulnerability Management
-
-
- OpenVAS
-
Source: https://www.openvas.org
OpenVAS is a framework of several services and tools that offer a comprehensive and powerful vulnerability scanning and vulnerability management solution. The framework is part of Greenbone Network’s commercial vulnerability management solution, developments from which have been contributed to the open-source community since 2009.
The actual security scanner is accompanied by a regularly updated feed of Network Vulnerability Tests (NVTs), over 50,000 in total.
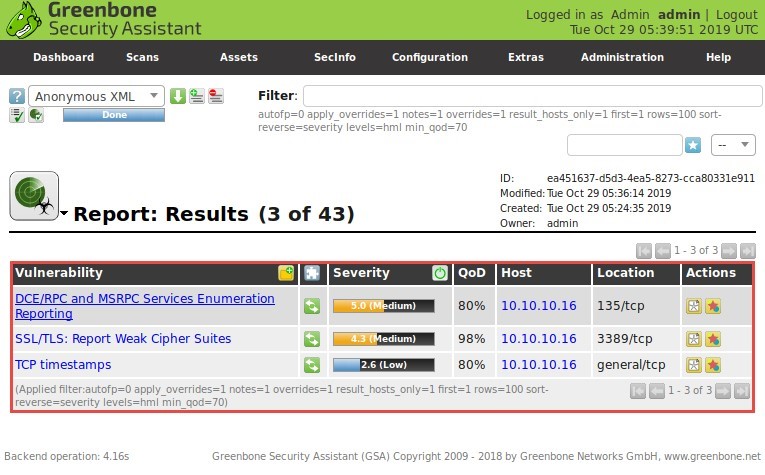
Figure 3.18: Vulnerability scanning using OpenVAS
-
-
- GFI LanGuard
-
Source: https://www.gfi.com
GFI LanGuard scans for, detects, assesses, and rectifies security vulnerabilities in a network and its connected devices. This is done with minimal administrative effort. It scans the operating systems, virtual environments, and installed applications through vulnerability check databases. It enables analysis of the state of network security, identifies risks, and offers solutions before the system can be compromised.

Figure 3.19: Vulnerability scanning using GFI LanGuard
Listed below are some of the additional vulnerability assessment tools:
- Nessus Professional (https://www.tenable.com)
- Nikto (https://cirt.net)
- Qualys FreeScan (https://freescan.qualys.com)
- Acunetix Web Vulnerability Scanner (https://www.acunetix.com)
- Nexpose (https://www.rapid7.com)
- Network Security Scanner (https://www.beyondtrust.com)
- SAINT Security Suite (https://www.carson-saint.com)
- beSECURE (AVDS) (https://www.beyondsecurity.com)
- Core Impact Pro (https://www.coresecurity.com)
- N-Stalker Web Application Security Scanner (https://www.nstalker.com)