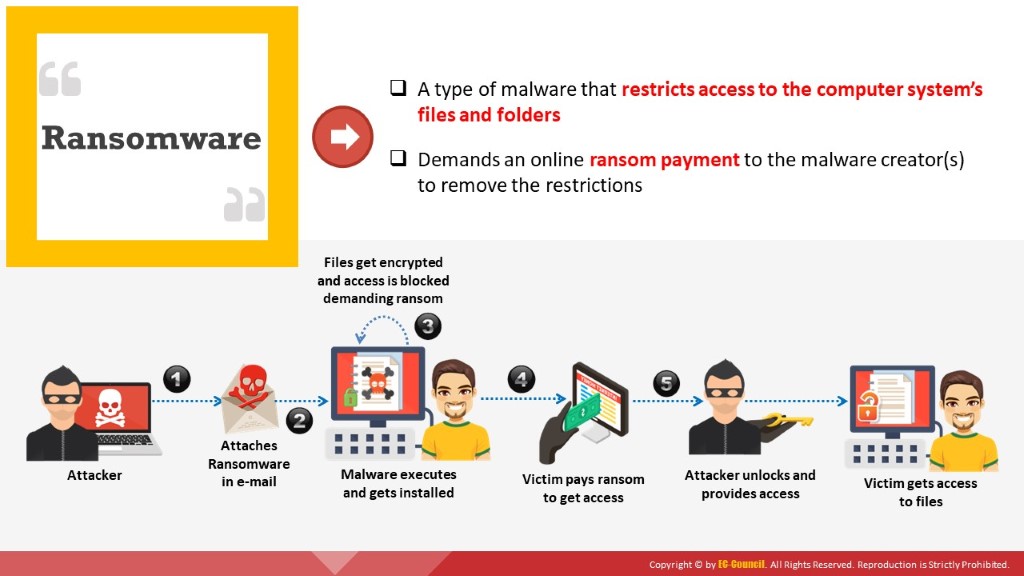
Ransomware is a type of malware that restricts access to the infected computer system or critical files and documents stored on it, and then demands an online ransom payment to the malware creator(s) to remove user restrictions. Ransomware is a type of crypto-malware that might encrypt files stored on the system’s hard disk or merely lock the system and display messages meant to trick the user into paying the ransom.
Usually, ransomware spreads as a Trojan, entering a system through email attachments, hacked websites, infected programs, app downloads from untrusted sites, vulnerabilities in network services, and so on. After execution, the payload in the ransomware runs and encrypts the victim’s data (files and documents), which can be decrypted only by the malware author. In some cases, user interaction is restricted using a simple payload.
In a web browser, a text file or webpage displays the ransomware demands. The displayed messages appear to be from companies or law enforcement personnel falsely claiming that the victim’s system is being used for illegal purposes or contains illegal content (e.g., porn videos, pirated software), or it could be a Microsoft product activation notice falsely claiming that installed Office software is fake and requires product re-activation. These messages entice victims into paying money to undo the restrictions imposed on them. Ransomware leverages victims’ fear, trust, surprise, and embarrassment to get them to pay the ransom demanded.
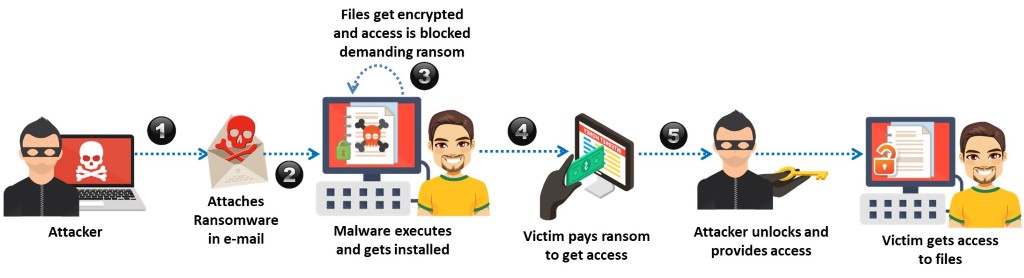
Figure 3.6: Depiction of ransomware attack
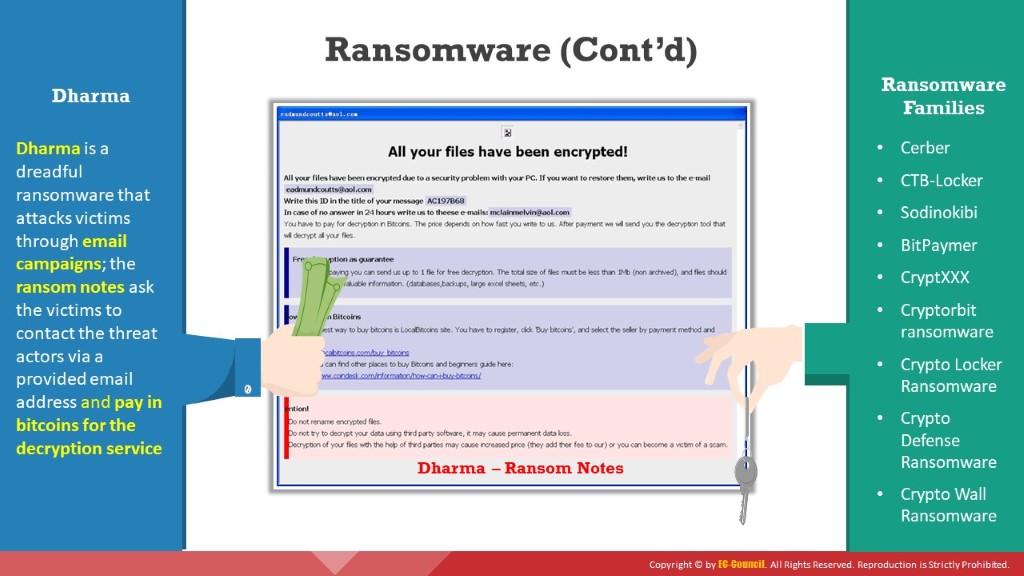
Ransomware Families
Listed below are some of the ransomware families:
-
- Cerber
- CTB-Locker
- Sodinokibi
- BitPaymer
- CryptXXX
- CryptorBit
- CryptoLocker
- CryptoDefense
- CryptoWall
- Police-themed Ransomware
Examples of Ransomware
-
-
- Dharma
-
Dharma is a dreadful ransomware that was first identified in 2016; since then, it has been affecting various targets across the globe with new versions. It has been regularly updated with sophisticated mechanisms in recent years. At the end of March 2019, Dharma struck a parking lot system in Canada. Previously, it also infected a Texas hospital and some other organizations. The variants of this ransomware have the following extension: .adobe, .bip, .combo, .cezar, .ETH, .java. Its encrypted files have new extensions, such as .xxxxx and .like. This ransomware employs an AES encryption algorithm to encrypt data and then displays ransom notes. These ransom notes are named as either Info.hta or FILES ENCRYPTED.txt. This ransomware carries out through email campaigns. The ransom notes ask victims to contact the threat actors via the provided email address and pay in bitcoins for the decryption service.

Figure 3.7: Screenshot displaying ransom demand message of Dharma ransomware
Some additional ransomware are as follows:
eCh0raix
SamSam
WannaCry
Petya - NotPetya
GandCrab
MegaCortex
LockerGoga
NamPoHyu
Ryuk
Cryptgh0st