Metasploit
Source: https://www.metasploit.com
The Metasploit Framework is a penetration-testing toolkit, exploit development platform, and research tool that includes hundreds of working remote exploits for various platforms. It performs fully automated exploitation of web servers by abusing known vulnerabilities and leveraging weak passwords via Telnet, SSH, HTTP, and SNM.
An attacker may use the following features of Metasploit to perform a web server attack:
Closed-loop vulnerability validation
Phishing simulations
Social engineering
Manual brute forcing
Manual exploitation
Evade-leading defensive solutions
Metasploit enables pen testers to perform the following:
Quickly complete pen-test assignments by automating repetitive tasks and leveraging multi-level attacks
Assess the security of web applications, network and endpoint systems, as well as email users
Tunnel any traffic through compromised targets to pivot deep into a network
Customize the content and template of executive, audit, and technical reports
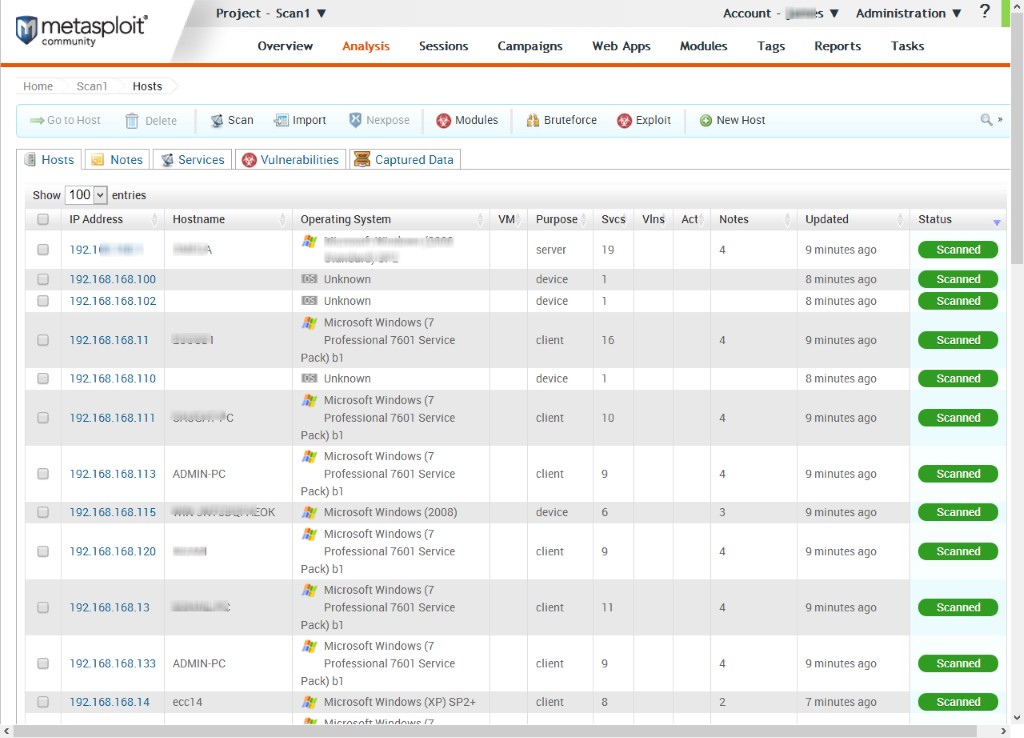
Figure 7.16: Screenshot of Metasploit
The following are some additional web server attack tools:
Immunity’s CANVAS (https://www.immunityinc.com)
THC Hydra (https://github.com)
HULK DoS (https://github.com)
MPack (https://sourceforge.net)
w3af (https://w3af.org)
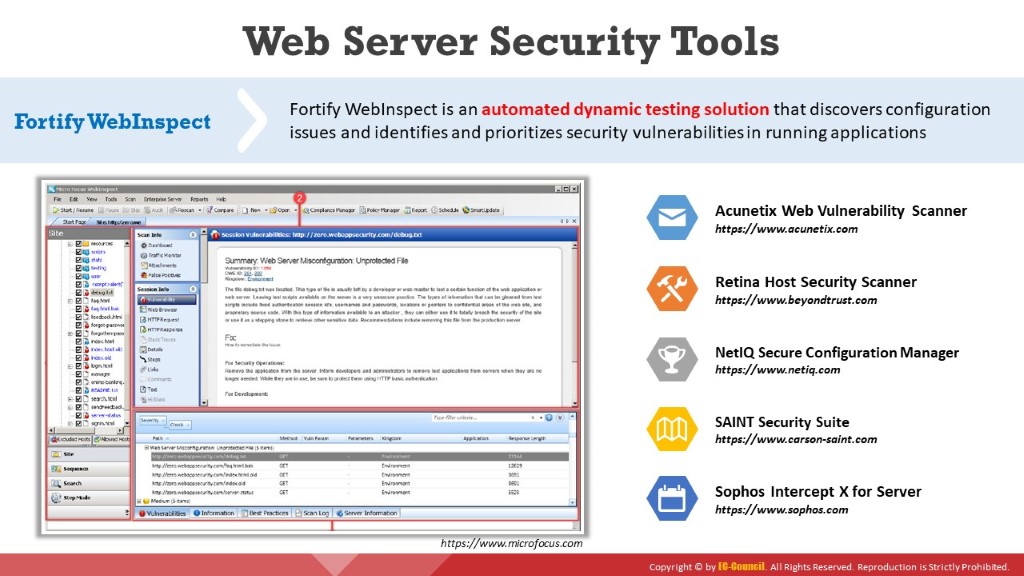
Fortify WebInspect
Source: https://www.microfocus.com
Fortify WebInspect is an automated dynamic testing solution that discovers configuration issues as well as identifies and prioritizes security vulnerabilities in running applications. It mimics real-world hacking techniques and provides a comprehensive dynamic analysis of complex web applications and services. WebInspect dashboards and reports provide organizations with visibility and an accurate risk posture of its applications.

Figure 7.17: Screenshot of Fortify WebInspect
The following are some additional web server security tools:
Acunetix Web Vulnerability Scanner (https://www.acunetix.com)
Retina Host Security Scanner (https://www.beyondtrust.com)
NetIQ Secure Configuration Manager (https://www.netiq.com)
SAINT Security Suite (https://www.carson-saint.com)
Sophos Intercept X for Server (https://www.sophos.com)


Earlier sections of this module discuss the different types of web-application attacks and threats that enable attackers to engage in successful attacks on target web applications. Later, the module discusses various web-application attack tools that attackers use to perform such attacks.
Burp Suite
Source: https://portswigger.net
Burp Suite is an integrated platform for performing security testing of web applications. It has various tools that work together to support the entire testing process, from initial mapping and analysis of an application's attack surface to finding and exploiting security vulnerabilities.
Burp Suite built-in tools
Intercepting proxy for inspecting and modifying traffic between your browser and the target application
Application-aware spider for crawling content and functionality
Web application scanner for automating the detection of numerous types of vulnerabilities
Intruder tool for performing customized attacks to find and exploit unusual vulnerabilities
Repeater tool for manipulating and resending individual requests
Sequencer tool for testing the randomness of session tokens

Figure 7.36: Screenshot of Burp Suite
OWASP Zed Attack Proxy
Source: https://www.owasp.org
OWASP Zed Attack Proxy (ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually. Attackers use OWASP ZAP for web spidering/crawling to identify hidden content and functionality in the target web application.

Figure 7.37: Screenshot of OWASP ZAP
Some additional web application attack tools are as follows:
Metasploit (https://www.metasploit.com)
w3af (http://w3af.org)
Nikto (https://cirt.net)
Sn1per (https://github.com)
WSSiP (https://github.com)

There are various web application security assessment tools available for scanning, detecting, and assessing the vulnerabilities/security of web applications. These tools reveal their security posture; you can use them to find ways to harden security and create robust web applications. Furthermore, these tools automate the process of accurate web application security assessment.
N-Stalker Web App Security Scanner
Source: https://www.nstalker.com
N-Stalker Web App Security Scanner checks for vulnerabilities such as SQL injection, XSS, and other known attacks. It is a useful security tool for developers, system/security administrators, IT auditors, and staff, as it incorporates the well-known “N-Stealth HTTP Security Scanner” and its database of 39,000 web attack signatures along with a component-oriented web application security assessment technology.

Figure 7.38: Screenshot of N-Stalker Web Application Security Scanner
Some additional web application security testing tools are as follows:
Acunetix WVS (https://www.acunetix.com)
Browser Exploitation Framework (BeEF) (http://beefproject.com)
Metasploit (https://www.metasploit.com)
PowerSploit (https://github.com)
Watcher (https://www.casaba.com)