Nmap
Source: https://nmap.org
Nmap ("Network Mapper") is a security scanner for network exploration and hacking. It allows you to discover hosts, ports, and services on a computer network, thus creating a "map" of the network. It sends specially crafted packets to the target host and then analyzes the responses to accomplish its goal. It scans vast networks of literally hundreds of thousands of machines. Nmap includes many mechanisms for port scanning (TCP and UDP), OS detection, version detection, ping sweeps, and so on.
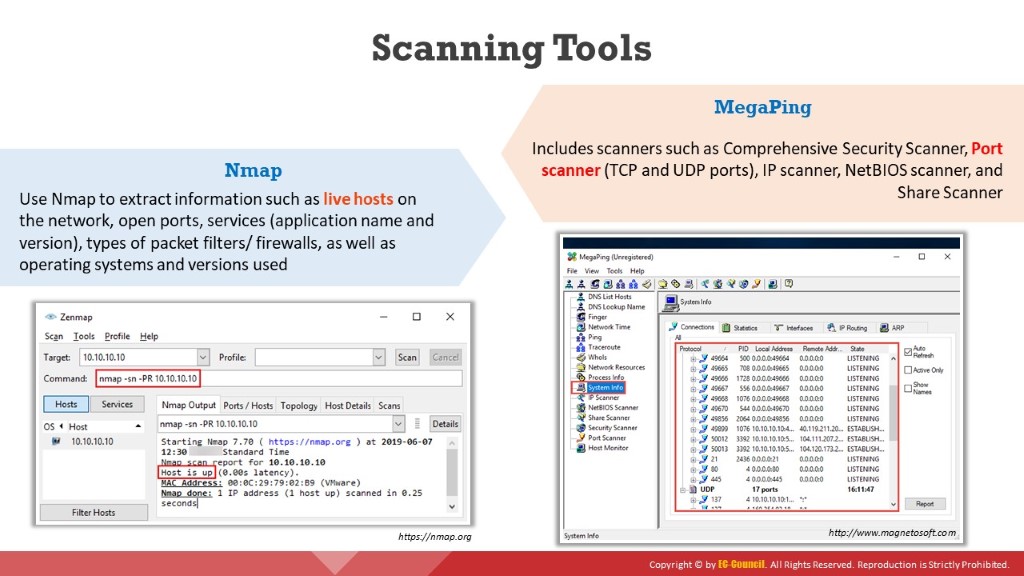
Either a security professional or an attacker can use this tool for their specific needs. Security professionals can use Nmap for network inventory, managing service upgrade schedules, and monitoring host or service uptime. Attackers use Nmap to extract information such as live hosts on the network, open ports, services (application name and version), type of packet filters/firewalls, MAC details, and OSs along with their versions.
Syntax: # nmap <options> <Target IP address>
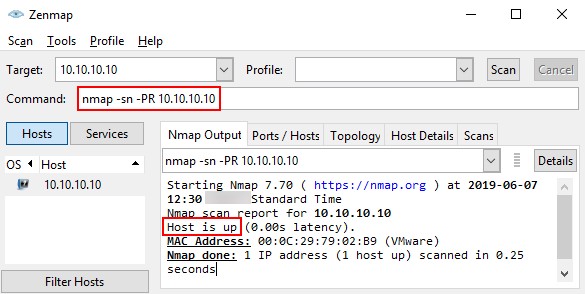
Figure 2.9: Screenshot displaying Nmap scan
MegaPing
Source: http://www.magnetosoft.com
MegaPing includes scanners such as Comprehensive Security Scanner, Port scanner (TCP and UDP ports), IP scanner, NetBIOS scanner, and Share Scanner. All Scanners can scan individual computers, any range of IP addresses, domains, and selected type of computers inside domains. MegaPing security scanner provides the following information: NetBIOS names, Configuration info, open TCP and UDP ports, Transports, Shares, Users, Groups, Services, Drivers, Local Drives, Sessions, and Remote Time of Date, Printers.
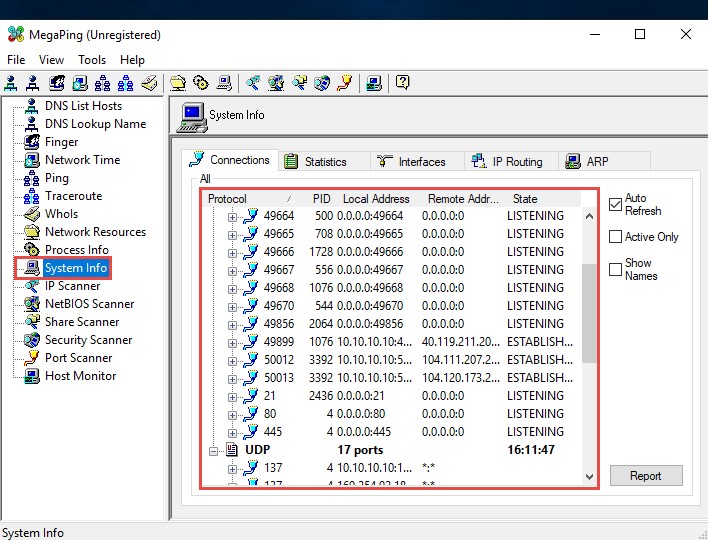
Figure 2.10: Screenshot displaying MegaPing scan
Unicornscan
Source: https://sourceforge.net
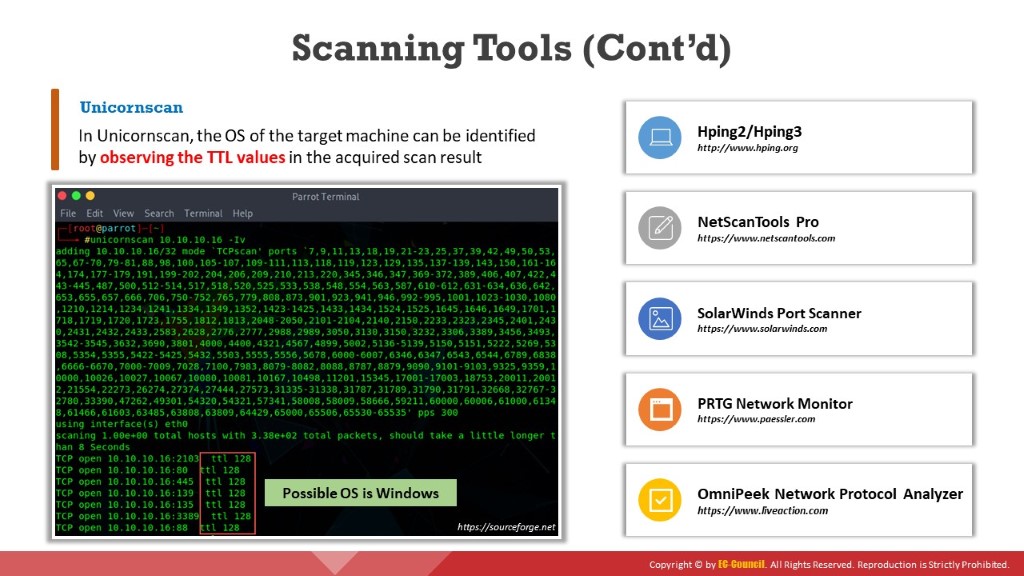
In Unicornscan, the OS of the target machine can be identified by observing the TTL values in the acquired scan result. To perform Unicornscan, the syntax #unicornscan <target IP address> is used. As shown in the screenshot, the ttl value acquired after the scan is 128; hence, the OS is possibly Microsoft Windows (Windows 7/8/8.1/10 or Windows Server 2008/12/16).
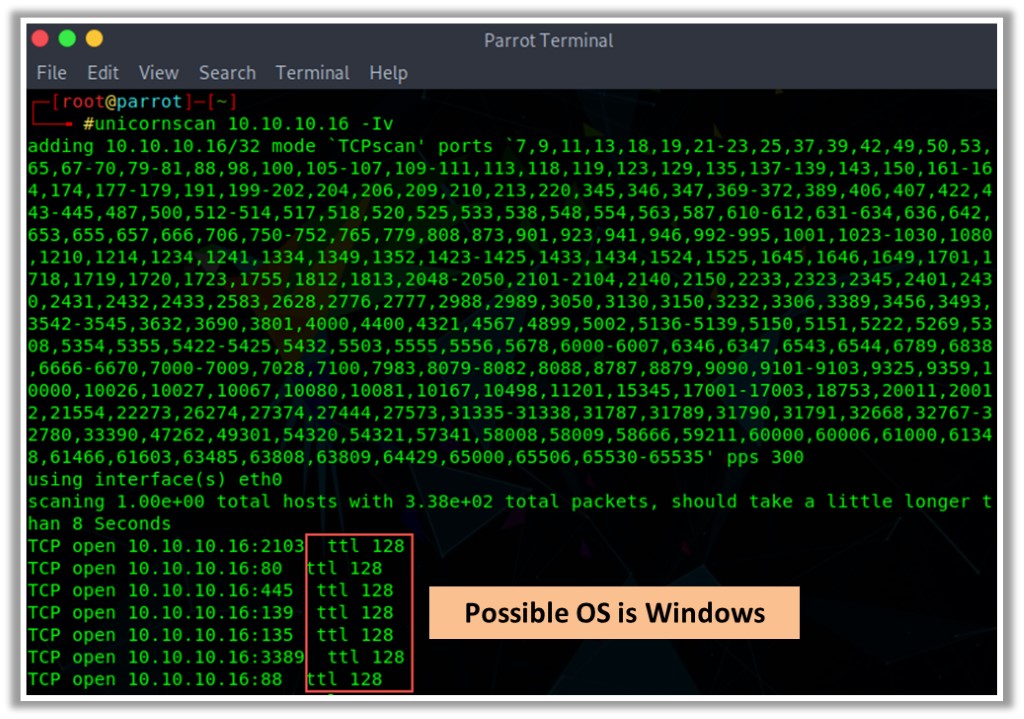
Figure 2.11: OS Discovery using Unicornscan
Some additional scanning tools are listed below:
Hping2/Hping3 (http://www.hping.org)
NetScanTools Pro (https://www.netscantools.com)
SolarWinds Port Scanner (https://www.solarwinds.com)
PRTG Network Monitor (https://www.paessler.com)
OmniPeek Network Protocol Analyzer (https://www.liveaction.com)