Cloud computing is an on-demand delivery of IT capabilities, in which IT infrastructure and applications are provided to subscribers as metered services over networks. Examples of cloud solutions include Google Cloud Platform, Amazon Web Service (AWS), Microsoft Azure, and IBM Cloud.
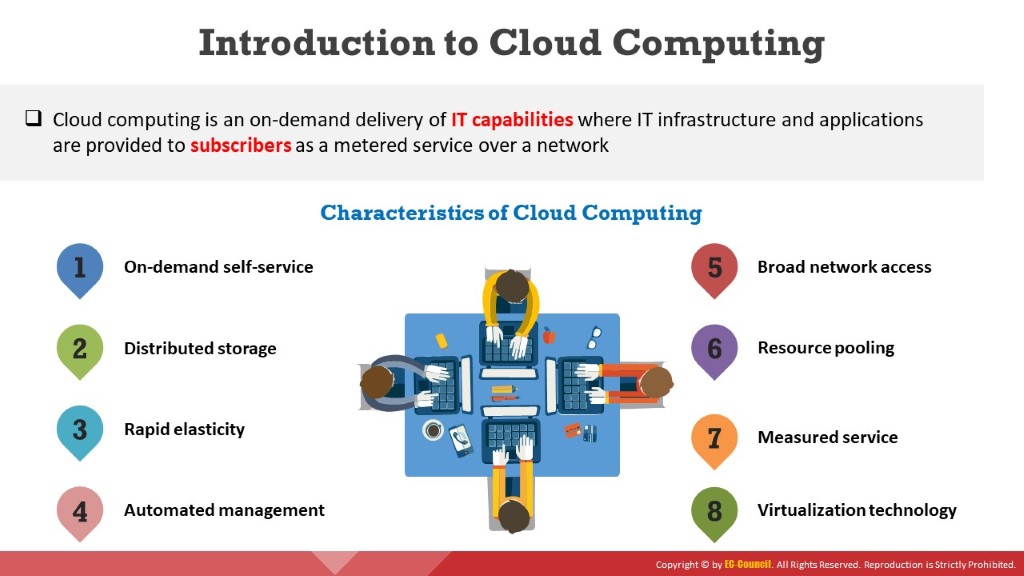
Characteristics of Cloud Computing
Discussed below are the characteristics of cloud computing that attract many businesses today to adopt cloud technology.
On-demand self-service: A type of service rendered by cloud service providers that allow provisions for cloud resources, such as computing power, storage, and network, always on-demand, without the need for human interaction with the service providers.Distributed storage: Distributed storage in the cloud offers better scalability, availability, and reliability of data. However, cloud distributed storage can potentially raise security and compliance concerns.
Rapid elasticity: The cloud offers instant provisioning of capabilities to rapidly scale up or down, according to demand. To the consumers, the resources available for provisioning seem to be unlimited and can be purchased in any quantity at any point of time.
Automated management: By minimizing user involvement, cloud automation speeds up the process and reduces labor costs and the possibility of human error.
Broad network access: Cloud resources are available over the network and accessed through standard procedures via a wide variety of platforms, including laptops, mobile phones, and personal digital assistants (PDAs).
Resource pooling: The cloud service provider pools all the resources together to serve multiple customers in the multi-tenant environment, with physical and virtual resources dynamically assigned and reassigned on demand by the consumer of the cloud.
Measured service: Cloud systems employ the “pay-per-use” metering method. Subscribers pay for cloud services by monthly subscription or according to the usage of resources such as storage levels, processing power, and bandwidth. Cloud service providers monitor, control, report, and charge consumption of resources by customers with complete transparency.
Virtualization technology: Virtualization technology in the cloud enables the rapid scaling of resources in a way that non-virtualized environments cannot achieve.
Limitations of Cloud Computing
Limited control and flexibility of organizationsProneness to outages and other technical issues
Security, privacy, and compliance issues
Contracts and lock-ins
Dependence on network connections
Potential vulnerability to attacks as every component is online
Difficulty in migrating from one service provider to another
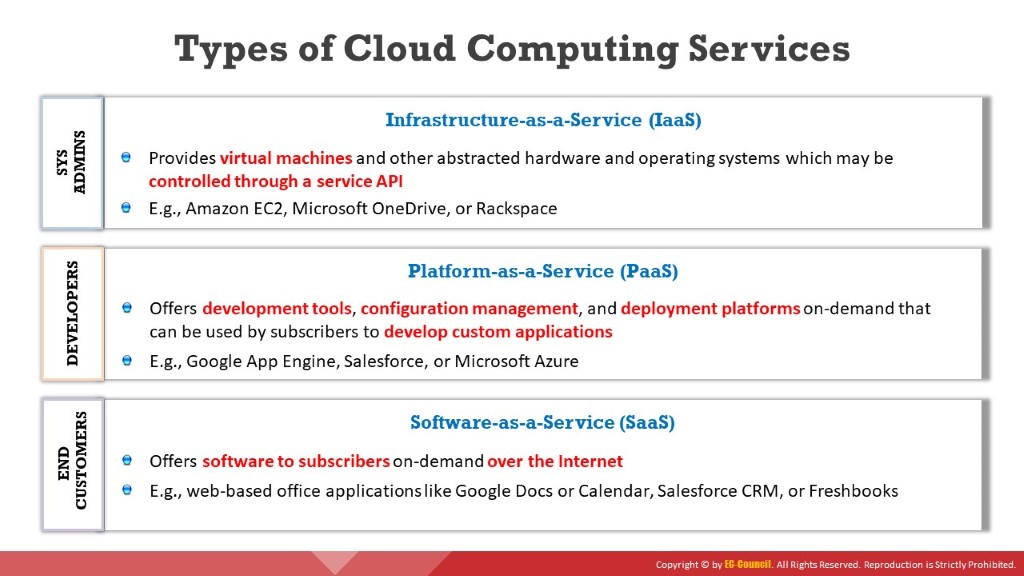
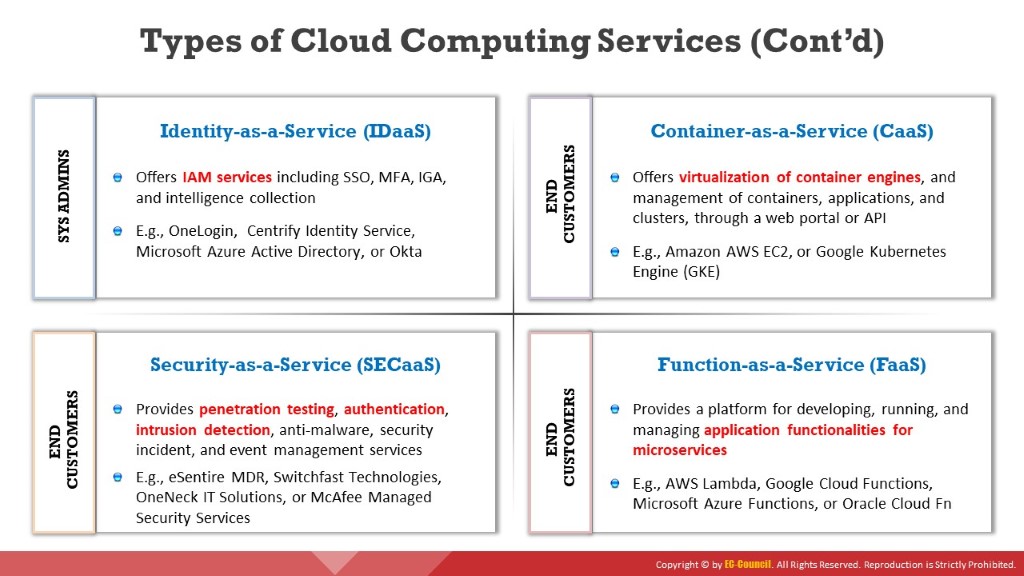
Cloud services are divided broadly into the following categories:
Infrastructure-as-a-Service (IaaS)
This cloud computing service enables subscribers to use on-demand fundamental IT resources, such as computing power, virtualization, data storage, and network. This service provides virtual machines and other abstracted hardware and operating systems (OSs), which may be controlled through a service application programming interface (API). As cloud service providers are responsible for managing the underlying cloud computing infrastructure, subscribers can avoid costs of human capital, hardware, and others (e.g., Amazon EC2, Microsoft OneDrive, Rackspace).
Advantages
Dynamic infrastructure scaling
Guaranteed uptime
Automation of administrative tasks
Elastic load balancing (ELB)
Policy-based services
Global accessibility
Disadvantages:
Software security is at high risk (third-party providers are more prone to attacks)
Performance issues and slow connection speeds
Platform-as-a-Service (PaaS)
This type of cloud computing service allows for the development of applications and services. Subscribers need not buy and manage the software and infrastructure underneath it but have authority over deployed applications and perhaps application hosting environment configurations. This offers development tools, configuration management, and deployment platforms on-demand, which can be used by subscribers to develop custom applications (e.g., Google App Engine, Salesforce, Microsoft Azure). Advantages of writing applications in the PaaS environment include dynamic scalability, automated backups, and other platform services, without the need to explicitly code for them.
Advantages
Simplified deployment
Prebuilt business functionality
Lower security risk compared to IaaS
Instant community
Pay-per-use model
Scalability
Disadvantages:
Vendor lock-in
Data privacy
Integration with the rest of the system applications
Software-as-a-Service (SaaS)
This cloud computing service offers application software to subscribers on-demand over the Internet. The provider charges for the service on a pay-per-use basis, by subscription, by advertising, or by sharing among multiple users (e.g., web-based office applications like Google Docs or Calendar, Salesforce CRM, and Freshbooks).
Advantages:
Low cost
Easy administration
Global accessibility
High compatibility (no specialized hardware or software is required)
Disadvantages:
Security and latency issues
Total dependency on the Internet
Switching between SaaS vendors is difficult
Identity-as-a-Service (IDaaS)
This cloud computing service offers authentication services to the subscribed enterprises and is managed by a third-party vendor to provide identity and access management services. It provides services such as Single-Sign-On (SSO), Multi-Factor-Authentication (MFA), Identity Governance and Administration (IGA), access management, and intelligence collection. These services allow subscribers to access sensitive data more securely both on and off-premises (e.g., OneLogin, Centrify Identity Service, Microsoft Azure Active Directory, Okta).
Advantages:
Low cost
Improved security
Simplify compliance
Reduced time
Central management of user accounts
Disadvantages:
Single server failure may disrupt the service or create redundancy on other authentication servers
Vulnerable to account hijacking attacks
Security-as-a-Service (SECaaS)
This cloud computing model integrates security services into corporate infrastructure in a cost-effective way. It is developed based on SaaS and does not require any physical hardware or equipment. Therefore, it drastically reduces the cost compared to that spent when organizations establish their own security capabilities. It provides services such as penetration testing, authentication, intrusion detection, anti-malware, security incident and event management (e.g., eSentire MDR, Switchfast Technologies, OneNeck IT Solutions, McAfee Managed Security Services).
Advantages:
Low cost
Reduced complexity
Continuous protection
Improved security through best security expertise
Latest and updated security tools
Rapid user provisioning
Greater agility
Increased time on core competencies
Disadvantages:
Increased attack surfaces and vulnerabilities
Unknown risk profile
Insecure APIs
No customization to business needs
Vulnerable to account hijacking attacks
Container-as-a-Service (CaaS)
This cloud computing model provides containers and clusters as a service to its subscribers. It provides services such as virtualization of container engines, management of containers, applications, and clusters through a web portal, or an API. Using these services, subscribers can develop rich scalable containerized applications through the cloud or on-site data centers. CaaS inherits features of both IaaS and PaaS (e.g., Amazon AWS EC2, Google Kubernetes Engine (GKE)).
Advantages:
Streamlined development of containerized applications
Pay-per-resource
Increased quality
Portable and reliable application development
Low cost
Few resources
Crash of application container does not affect other containers
Improved security
Improved patch management
Improved response to bugs
High scalability
Streamlined development
Disadvantages:
High operational overhead
Platform deployment is the developer’s responsibility
Function-as-a-Service (FaaS)
This cloud computing service provides a platform for developing, running, and managing application functionalities without the complexity of building and maintaining necessary infrastructure (serverless architecture). This model is mostly used while developing applications for microservices. It provides on-demand functionality to the subscribers that powers off the supporting infrastructure and incurs no charges when not in use. It provides data processing services, such as Internet of Things (IoT) services for connected devices, mobile and web applications, and batch-and-stream processing (e.g., AWS Lambda, Google Cloud Functions, Microsoft Azure Functions, Oracle Cloud Fn).
Advantages:
Pay-per-use
Low cost
Efficient security updates
Easy deployment
High scalability
Disadvantages:
High latency
Memory limitations
Monitoring and debugging limitations
Unstable tools and frameworks
Vendor lock-in
Cloud deployment model selection is based on enterprise requirements. One can deploy cloud services in different ways, according to the factors given below:
Host location of cloud computing services
Security requirements
Sharing of cloud services
Ability to manage some or all of the cloud services
Customization capabilities
The five standard cloud deployment models are
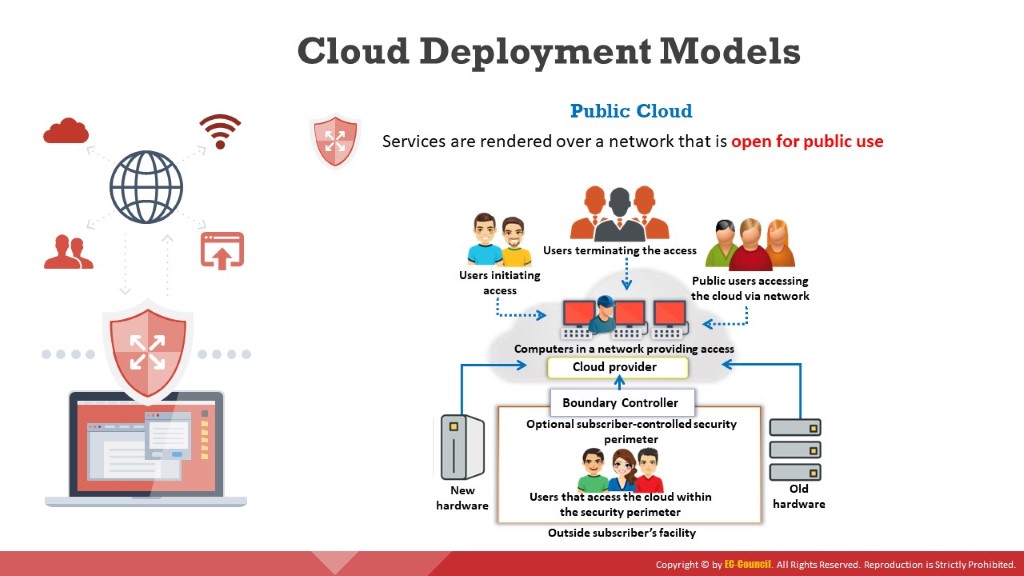
Public Cloud
In this model, the provider makes services such as applications, servers, and data storage available to the public over the Internet. Therefore, he is liable for the creation and constant maintenance of the public cloud and its IT resources. Public cloud services may be free or based on a pay-per-usage model (e.g., Amazon Elastic Compute Cloud (EC2), Google App Engine, Microsoft Azure, IBM Cloud).
1. Advantages:
Simplicity and efficiency
Low cost
Reduced time (when server crashes, needs to restart or reconfigure cloud)
No maintenance (public cloud service is hosted off-site)
No contracts (no long-term commitments)
2. Disadvantages:
Security is not guaranteed
Lack of control (third-party providers are in charge)
Slow speed (relies on Internet connections; the data transfer rate is limited)
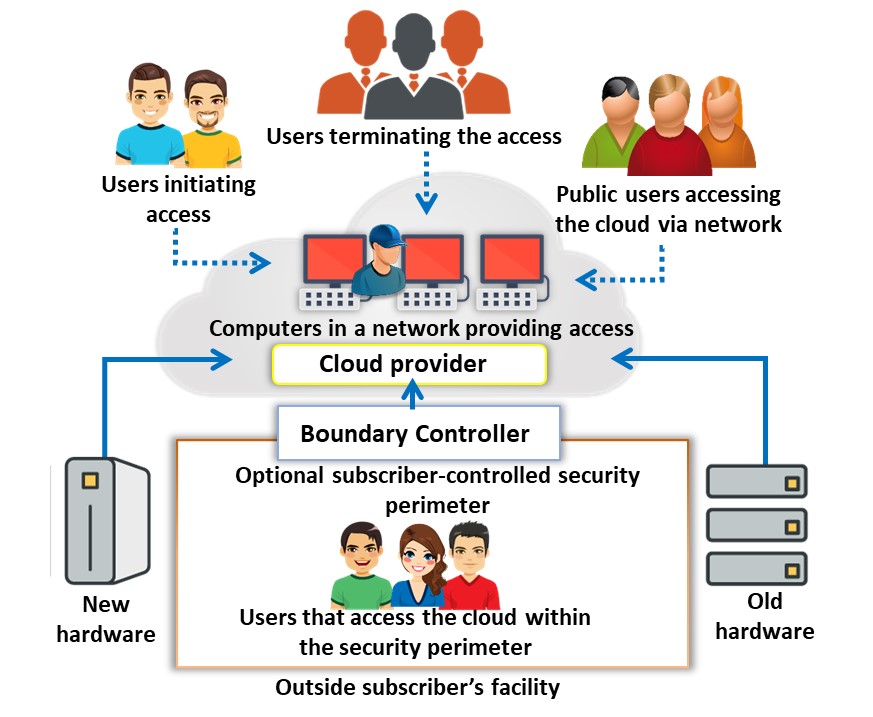
Figure 11.2: Public cloud deployment model
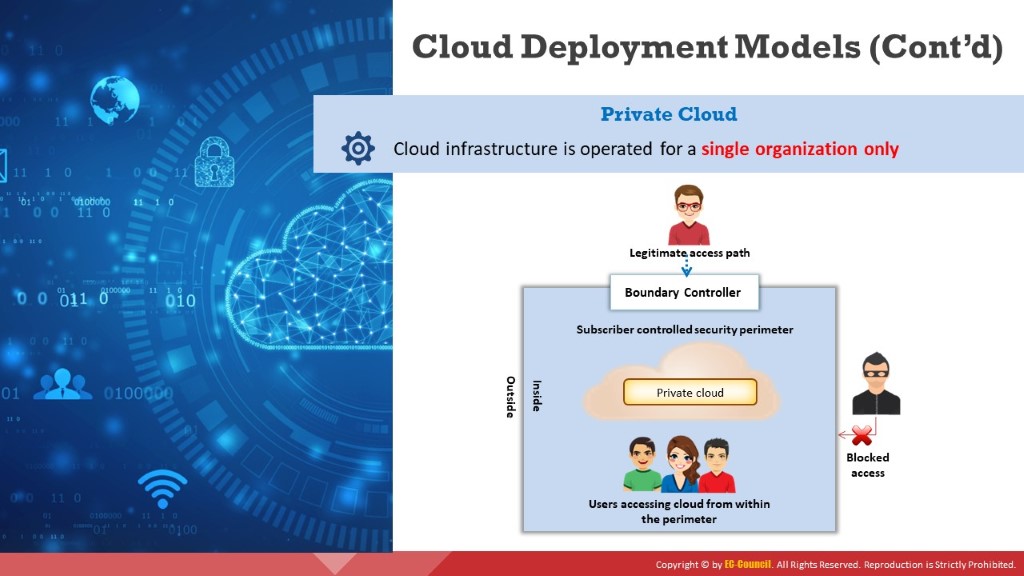
Private Cloud
A private cloud, also known as the internal or corporate cloud, is a cloud infrastructure operated by a single organization and implemented within a corporate firewall. Organizations deploy private cloud infrastructures to retain full control over corporate data (e.g., BMC Software, VMware vRealize Suite, SAP Cloud Platform).
1. Advantages:
Security enhancement (services are dedicated to a single organization)
Increased control over resources (organization is in charge)
High performance (cloud deployment within the firewall implies high data transfer rates)
Customizable hardware, network, and storage performances (as the organization owns private cloud)
Sarbanes Oxley, PCI DSS, and HIPAA compliance data are much easier to attain
2. Disadvantages:
High cost
On-site maintenance
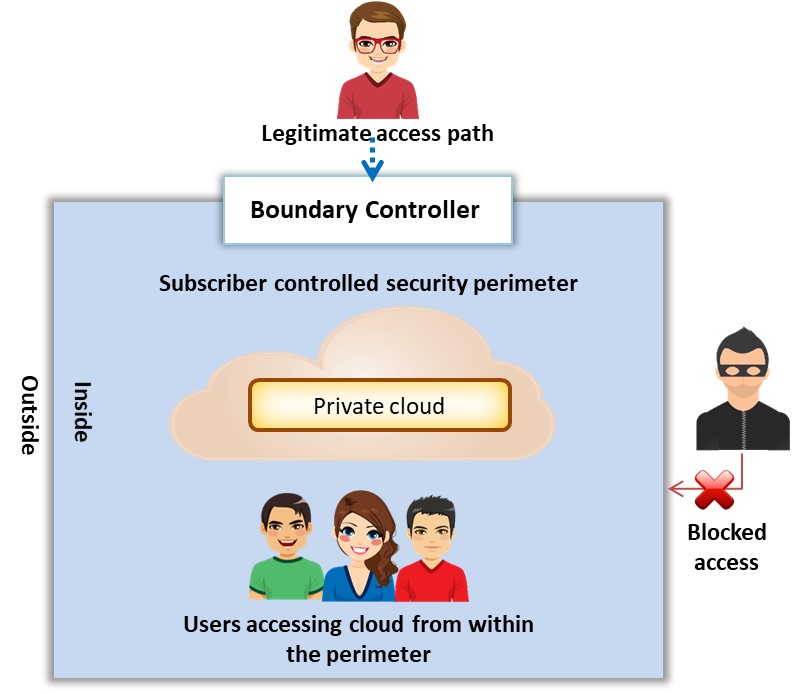
Figure 11.3: Private cloud deployment model
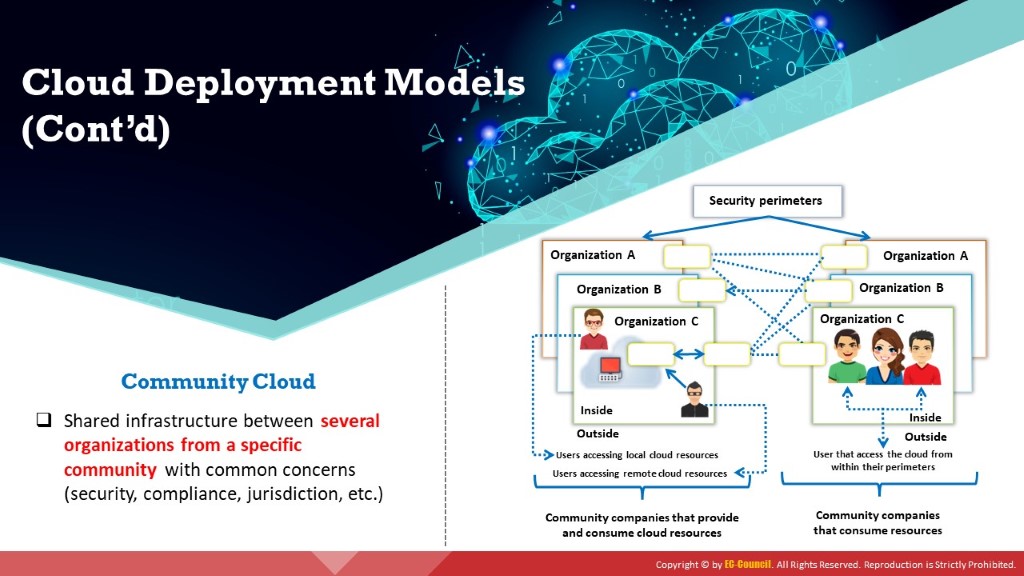
Community Cloud
It is a multi-tenant infrastructure shared among organizations from a specific community with common computing concerns, such as security, regulatory compliance, performance requirements, and jurisdiction. The community cloud can be either on- or off-premises and governed by the participated organizations or by a third-party managed service provider (e.g., Optum Health Cloud, Salesforce Health Cloud).
1. Advantages:
Less expensive compared to the private cloud
Flexibility to meet the community’s needs
Compliance with legal regulations
High scalability
Organizations can share a pool of resources from anywhere via the Internet
2. Disadvantages:
Competition between consumers in resource usage
Inaccurate prediction of required resources
Lack of legal entity in case of liability
Moderate security (other tenants may be able to access data)
Trust and security concerns between tenants
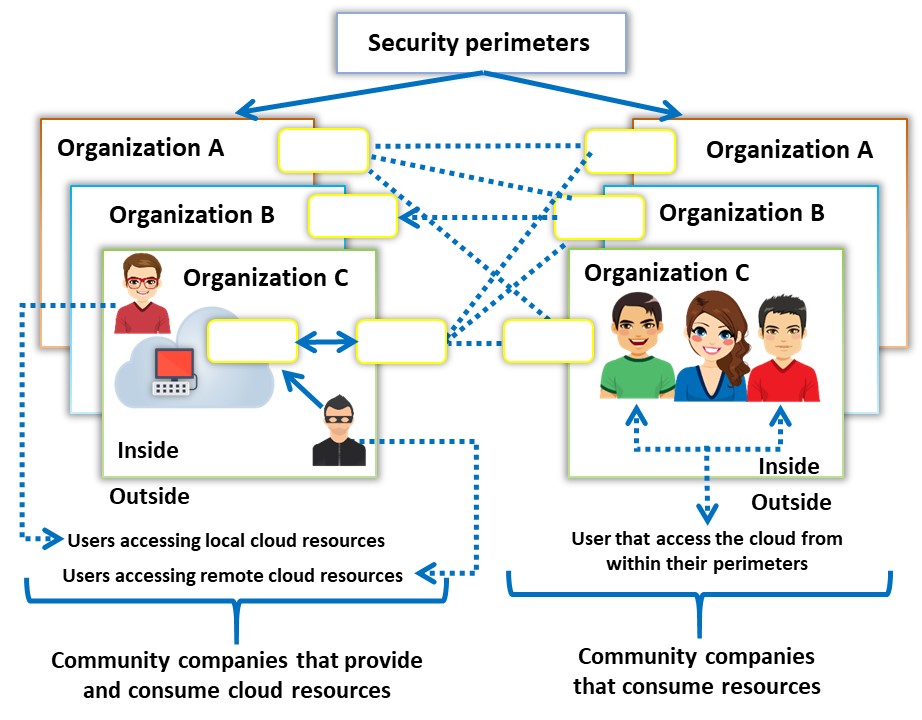
Figure 11.4: Community cloud deployment model
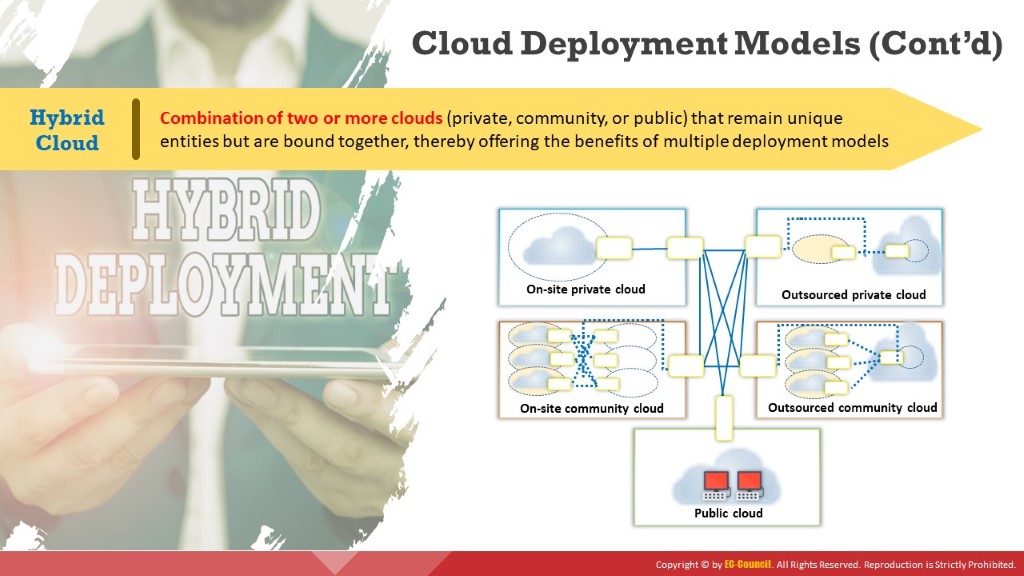
Hybrid Cloud
It is a cloud environment comprised of two or more clouds (private, public, or community) that remain unique entities but are bound together to offer the benefits of multiple deployment models. In this model, the organization makes available and manages some resources in-house and provides other resources externally (e.g., Microsoft Azure, Zymr, Parangat, Logicalis).
Example: An organization performs its critical activities on the private cloud (e.g., operational customer data) and non-critical activities on the public cloud.
1. Advantages:
High scalability (contains both public and private clouds)
Offers both secure and scalable public resources
High level of security (comprises private cloud)
Allows to reduce and manage the cost according to requirements
2. Disadvantages:
Communication at the network level may be conflicted as it uses both public and private clouds
Difficult to achieve data compliance
Organization reliant on the internal IT infrastructure in case of outages (maintain redundancy across data centers to overcome)
Complex service level agreements (SLAs)
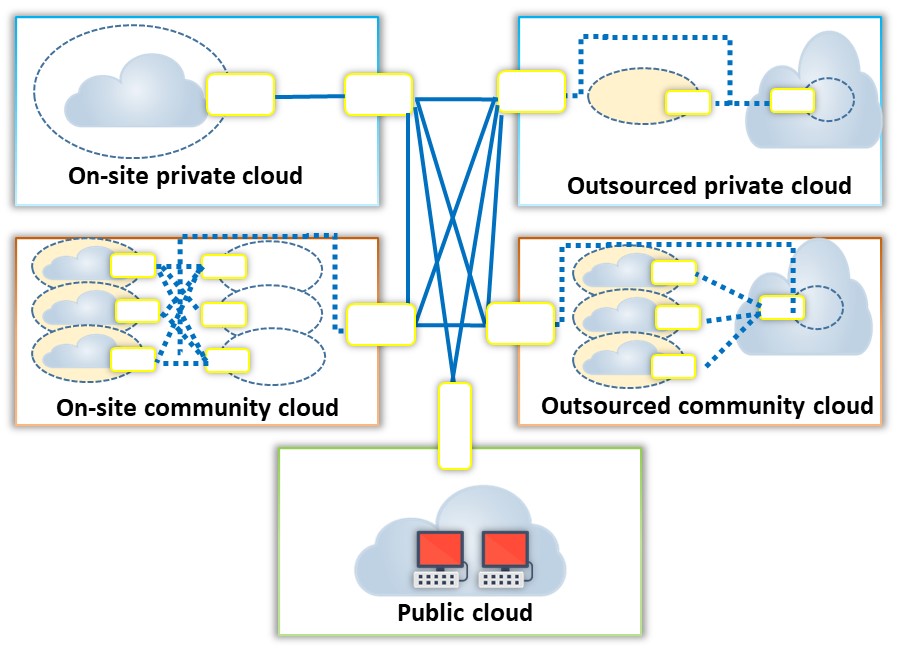
Figure 11.5: Hybrid cloud deployment model
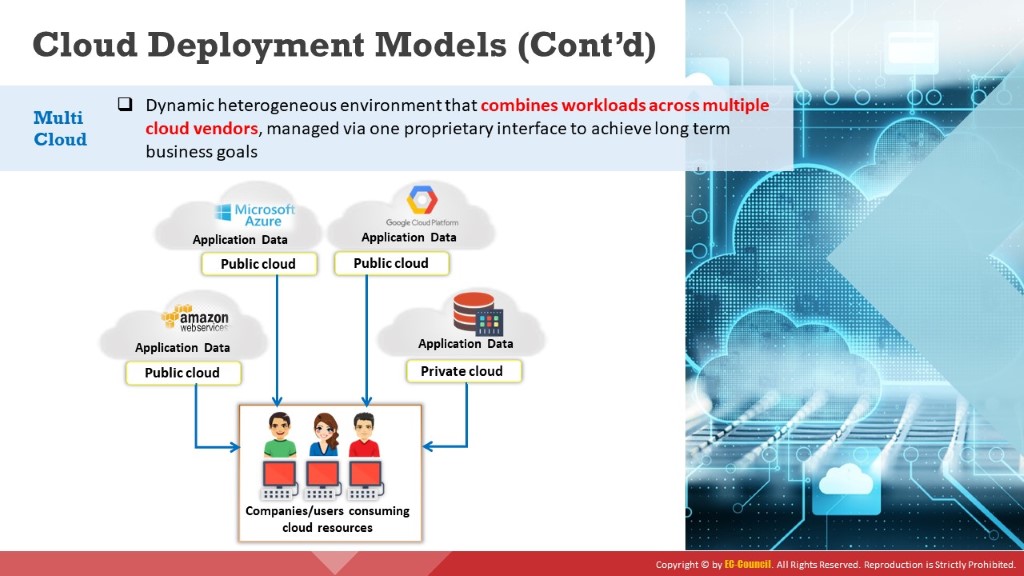
Multi Cloud
It is a dynamic heterogeneous environment that combines workloads across multiple cloud vendors that are managed via one proprietary interface to achieve long-term business goals. The multi cloud uses multiple computing and storage services from different cloud vendors. It distributes cloud assets, software, applications, etc. across various cloud-hosting environments. Multi cloud environments are mostly all-private, all-public or a combination of both. Organizations use multi cloud environments for distributing computing resources, thereby increasing computing power and storage capabilities, and limiting the data loss and downtime risk to a great extent (e.g., Microsoft Azure Arc, AWS Kaavo IMOD, Google Cloud Anthos).
1. Advantages:
High reliability and low latency
Flexibility to meet business needs
Cost-performance optimization and risk mitigation
Low risk of distributed denial-of-service (DDoS) attacks
Increased storage availability and computing power
Low probability of vendor lock-in
2. Disadvantages:
Multi-cloud system failure affects business agility
Using more than one provider causes redundancy
Security risks due to complex and large attack surface
Operational overhead
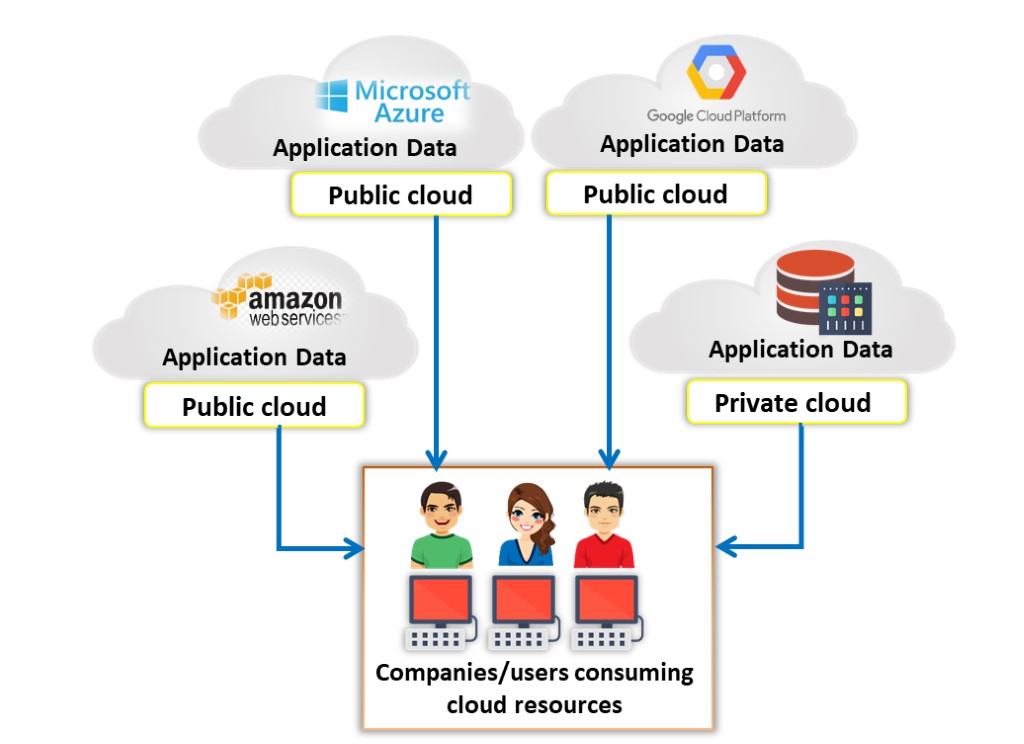
Figure 11.6: Multi cloud deployment model
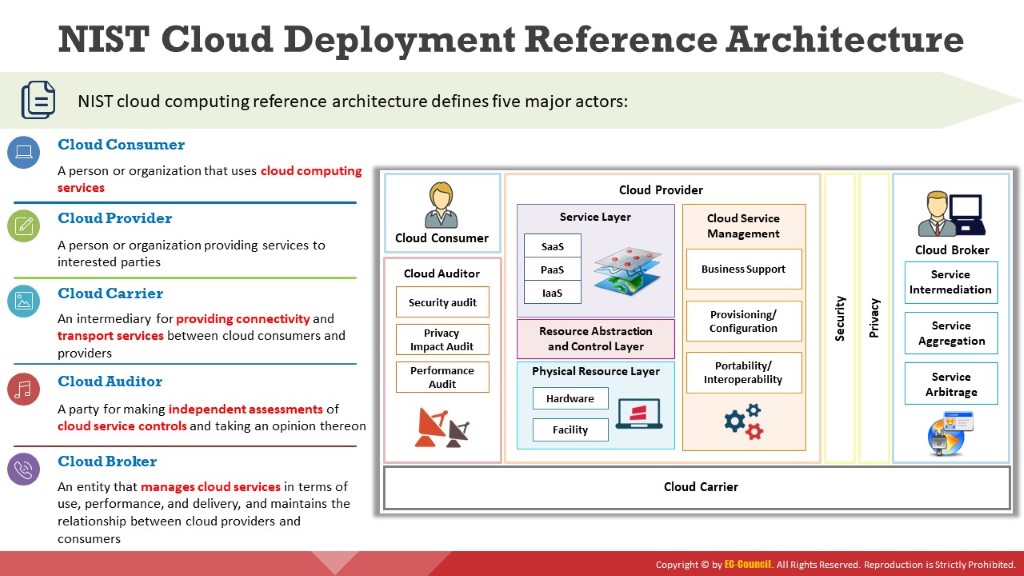
The figure below gives an overview of the NIST cloud computing reference architecture; it displays the primary actors, activities, and functions in cloud computing. The diagram illustrates a generic high-level architecture, intended for better understanding the uses, requirements, characteristics, and standards of cloud computing.
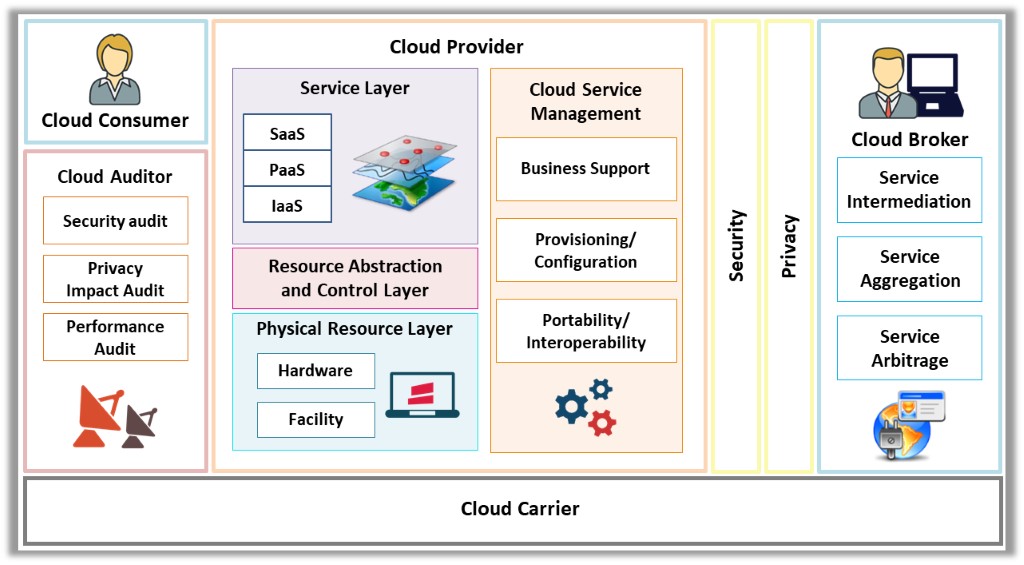
Figure 11.7: NIST cloud computing reference architecture
The five significant actors are as follows:
Cloud Consumer
A cloud consumer is a person or organization that maintains a business relationship with the cloud service providers (CSPs) and utilizes the cloud computing services. The cloud consumer browses the CSP’s service catalog requests for the desired services, sets up service contracts with the CSP (either directly or via cloud broker), and uses the services. The CSP bills the consumer based on the services provided. The CSP should fulfill the service level agreement (SLA) in which the cloud consumer specifies the technical performance requirements, such as the quality of service, security, and remedies for performance failure. The CSP may also define limitations and obligations if any, that cloud consumers must accept.
The services available to a cloud consumer in the PaaS, IaaS, and SaaS models are as follows:
PaaS – database (DB), business intelligence, application deployment, development and testing, and integration
IaaS – storage, services management, content delivery network (CDN), platform hosting, backup and recovery, and computing
SaaS – human resources, enterprise resource planning (ERP), sales, customer relationship management (CRM), collaboration, document management, email and office productivity, content management, financial services, and social networks.
Cloud Provider
A cloud provider is a person or organization who acquires and manages the computing infrastructure intended for providing services (directly or via a cloud broker) to interested parties via network access.
Cloud Carrier
A cloud carrier acts as an intermediary that provides connectivity and transport services between CSPs and cloud consumers. The cloud carrier provides access to consumers via a network, telecommunication, or other access devices.
Cloud Auditor
A cloud auditor is a party that performs an independent examination of cloud service controls to express an opinion thereon. Audits verify adherence to standards through a review of the objective evidence. A cloud auditor can evaluate the services provided by a CSP regarding security controls (management, operational, and technical safeguards intended to protect the confidentiality, integrity, and availability of the system and its information), privacy impact (compliance with applicable privacy laws and regulations governing an individual’s privacy), performance, etc.
Cloud Broker
The integration of cloud services is becoming too complicated for cloud consumers to manage. Thus, a cloud consumer may request cloud services from a cloud broker, rather than directly contacting a CSP. The cloud broker is an entity that manages cloud services regarding use, performance, and delivery and maintains the relationship between CSPs and cloud consumers.
The services provided by cloud brokers fall in three categories:
1. Service Intermediation
Improves a given function by a specific capability and provides value-added services to cloud consumers.
2. Service Aggregation
Combines and integrates multiple services into one or more new services.
3. Service Arbitrage
Similar to service aggregation but without the fixing of the aggregated services (the cloud broker can choose services from multiple agencies).